Thijs Laarhoven
Cryptographer at NXP
Welcome
Welcome to my homepage! My name is Thijs Laarhoven, and I am currently a principal cryptographer at NXP Semiconductors in Eindhoven, The Netherlands. Before this, I was a research scientist at TNO, the Dutch Organization for Applied Scientific Research, in The Hague, The Netherlands. Before that, I was a postdoctoral researcher at the Eindhoven University of Technology, in the Netherlands. During this postdoc, I held a temporary visiting scientist position at the University of California, Berkeley, for the Spring 2020 semester. Prior to that, I was a postdoctoral researcher at IBM Research in Zurich, Switzerland. Before that, I completed my PhD at the Eindhoven University of Technology, in the Netherlands. And before that, I completed my MSc with a graduation project at Irdeto< in Eindhoven, The Netherlands.
Research
Statistics
Citations
2300+Publications
50+Talks
60+Chess title
FMResume
Summary
Besides being able to work independently and setting my own agenda, one of my strengths is to find the right perspective for a complex task, and to see how techniques from other areas can be used to solve these problems efficiently. For instance, in my paper at Crypto 2015 I made a new connection between lattice algorithms and nearest neighbor searching, marking the beginning of a long line of new work on this topic.
Experience
Aug 2023 - present

Principal Cryptographer
As one of the leading chip manufacturing companies in the world, NXP is committed to providing strong security solutions on chips, keeping in mind the limited computational capabilities of chips for ensuring security in untrusted environments. Apart from existing threats and solutions, NXP is also working hard on a smooth transition to quantum-secure solutions in the near future. My contributions involve providing expertise on quantum-safe cryptography, as well as getting involved with the transition from theoretical solutions to actual secure implementations of these schemes.
Dec 2021 - Jul 2023

Research Scientist
At TNO, the Dutch Organization for Applied Scientific Research, I contribute to bringing digital security innovations from the lab into the field. This involves going beyond academic research, seeing how technologies can land in society and make a positive impact in government or industry settings, and demonstrating their added value through proof-of-concept demonstrations of the technology. Focus areas at TNO include the migration to quantum-safe cryptography, and finding ways to collaborate on privacy-sensitive distributed data with tools such as multiparty computation and (fully) homomorphic encryption.
Nov 2017 - Nov 2021

Postdoctoral Researcher
For my postdoc at the TU/e I studied topics related to lattices and nearest neighbor searching, in the context of lattice-based (post-quantum) cryptography, and for various applications that require finding similar items in large databases. For the period 2019-2021, this research was funded by a three-year personal NWO Veni innovational research grant of EUR 250.000, which supports outstanding researchers to pursue their line of research for three years at any Dutch university.
Jan 2020 - May 2020

Visiting Scientist
During Spring 2020 I was an invited visiting scientist to the research program titled "Lattices: Algorithms, Complexity, and Cryptography" at the Simons Institute for the Theory of Computing. During this program, researchers visited from all around the world to collaborate on open questions in lattice algorithms and lattice-based cryptography, and to discuss ideas and potential new approaches, until in March 2020 the world went into lockdown, and the program came to an early end.
Mar 2016 - Sep 2017

Postdoctoral Researcher
During my time at the IBM Research lab in Zurich, Switzerland, I studied methods to further improve lattice-based cryptographic solutions, as well as methods that attempt to break these schemes, to get a better understanding of the true security of these lattice-based schemes. I further continued my research on efficient nearest neighbor techniques, which resulted in a nice joint paper on practical and optimal time-space trade-offs.
Oct 2011 - Feb 2016

Doctoral Candidate
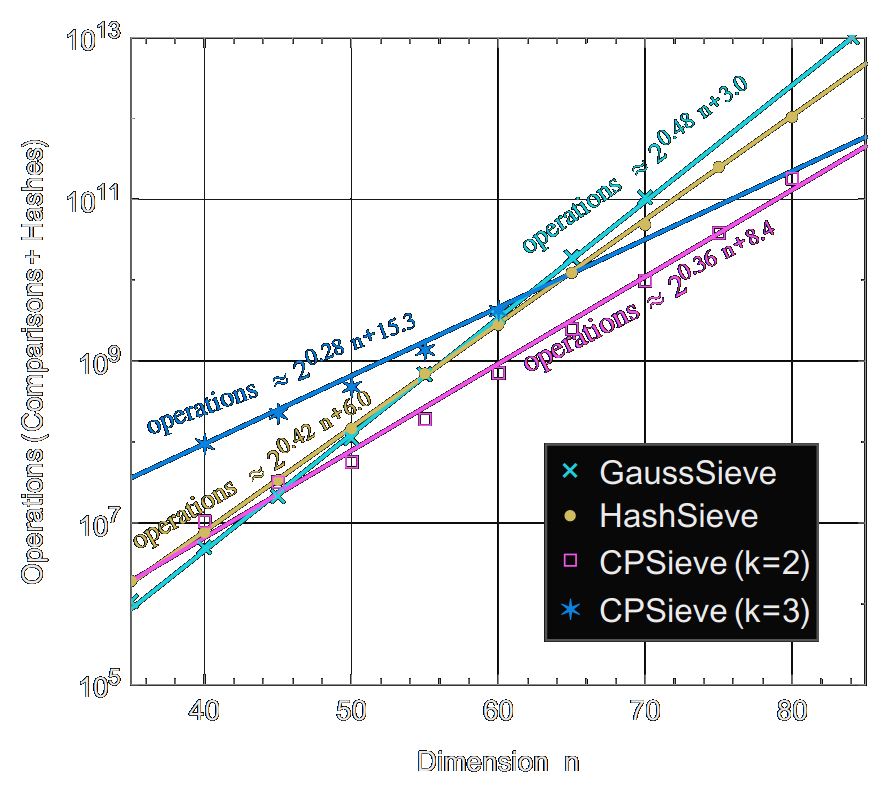
In my PhD research, I focused on obtaining a better understanding of, and finding improvements for, various lattice algorithms that lie at the foundation of lattice-based cryptanalysis. Specifically, I focused on lattice sieving methods for the shortest vector problem, and I helped transform sieving from a mostly irrelevant theoretical novelty (2011) to the main algorithm to consider when choosing parameters (2016). The time complexity 20.292n + o(n) from our SODA 2016 paper currently still stands as the asymptotically fastest method for solving the shortest vector problem in high dimensions, while the 20.265n + o(n) from my PhD thesis was long the best quantum complexity for the shortest vector problem, until it was finally improved by Chailloux-Loyer at AsiaCrypt 2021.
Oct 2010 - Jun 2011

Research Intern
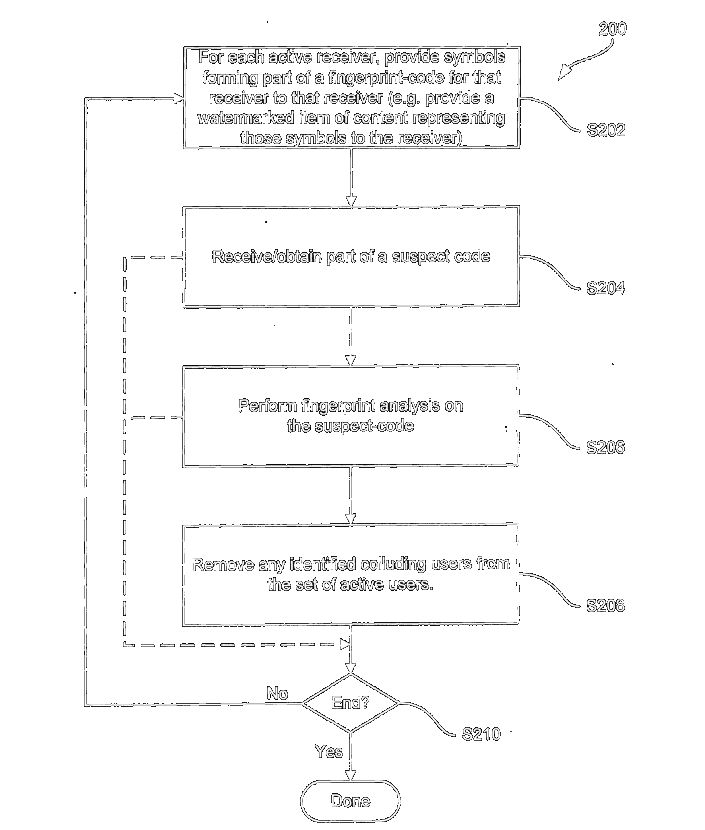
To protect copyrighted content against piracy, fingerprints or watermarks are commonly embedded in the content, allowing the distributor of the content to trace a pirate copy to the responsible user. To combat this solution, several pirates may collude, and mix their watermarked copies into a new copy, with a fingerprint which is a mix of the individual pirates' fingerprints. With fingerprinting codes it is possible to find the pirates even if they collude. Various previous solutions were aimed at non-adaptive settings, and during my internship I studied adaptive solutions, leading to the invention of the (patented) dynamic Tardos scheme.
Volunteering
Oct 2020 - Dec 2021

Lichess.org Team Member
Lichess is the second largest online chess site, and each day millions of games are played between users from all around the world. Lichess is free, open-source, ad-free, and exists as a non-profit organization funded solely through donations from users. As a team member I assisted with moderating the chat, finding cheaters, handling ban appeals, developing improved cheat detection tools, scouting and guiding new team members, and outlining the path towards the future for Lichess in terms of policies, governance, goals, vision, and more.
Education
Oct 2011 - Feb 2016

PhD in Cryptography (cum laude)
The research in my PhD at the Eindhoven University of Technology (TU/e) focused on two topics: improving collusion-resistant fingerprinting schemes, and a new direction in lattice sieving algorithms by combining them with nearest neighbor search techniques. Besides the results in these two main topics, I showed how to improve upon the state-of-the-art for group testing and nearest neighbor searching. The resulting PhD thesis titled Search problems in cryptography: From fingerprinting to lattice sieving from December 2015 can be downloaded here.
Sep 2009 - Aug 2011

MSc in Applied Mathematics (cum laude)
I graduated in the group Coding Theory and Cryptology, which is part of the section Discrete Mathematics. In the second year of my Masters I did a final project combined with an internship at Irdeto BV. This internship concluded with writing a Masters thesis, titled Collusion-resistant traitor tracing schemes, which can be downloaded here.
Sep 2006 - Aug 2009

BSc in Applied Mathematics (cum laude)
During the first three years of my studies I took various courses in both Applied Mathematics and in Computer Science. In the first year I obtained propaedeutic diplomas in both Mathematics and Computer Science, and later I also completed a so-called "minor" in Advanced Computer Science. The last part of these three years focused on discrete mathematics, which concluded with a final project and thesis about the Collatz conjecture. This thesis titled The 3n+1 conjecture can be downloaded here.
Skills
- Python
- C
- C++
- Object Pascal
- Java
- Haskell
- HTML
- PHP
- SQL
- CSS
- JavaScript
- Mathematica
- R
- Matlab
- Sage
- Microsoft Office
- LaTeX
- Git
- Dutch
- English
- French
- German
Publications
Filters
- All
- ⭐ Selected
- 🏆 Awards
- 👥 Conferences
- 📄 Journals
- 📗 Theses
- 💡 Patents
- 2023
- 2022
- 2021
- 2020
- 2019
- 2018
- 2017
- 2016
- 2015
- 2014
- 2013
- 2012
- 2011
- 2010
- 2009
- Lattices
- Codes
- Quantum
- Nearest neighbors
- Traitor tracing
- Group testing
- Collatz conjecture
- Chess
Papers
Oblivious graph algorithms for TSP and VRP using FHE and MPC
Sam Leder, Thijs LaarhovenPreprint, 2023 Preprint, 2023
The irreducible vectors of a lattice
Emmanouil Doulgerakis, Thijs Laarhoven, Benne de WegerDesigns, Codes and Cryptography 2023 Designs, Codes and Cryptography 2023
Human and computer decision-making in chess with applications to online cheat detection
Thijs Laarhoven, Aditya PonukumatiCG 2022 CG 2022
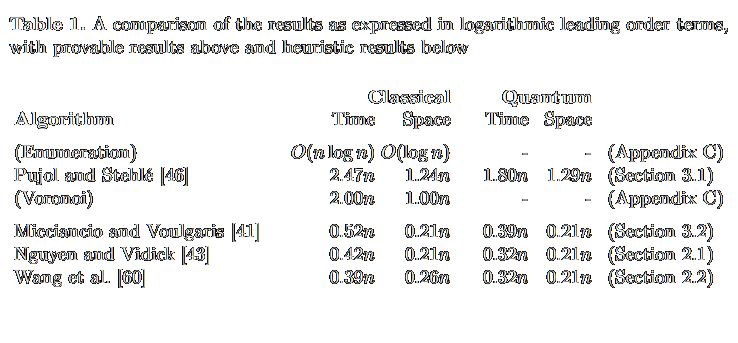
Lower bounds for nearest neighbor searching and post-quantum cryptanalysis
Elena Kirshanova, Thijs LaarhovenCrypto 2021 Crypto 2021
Dual lattice attacks for closest vector problems (with preprocessing)
Thijs Laarhoven, Michael WalterCT-RSA 2021 CT-RSA 2021
Approximate Voronoi cells for lattices, revisited
Thijs LaarhovenJournal of Mathematical Cryptology 2020 Journal of Mathematical Cryptology 2020
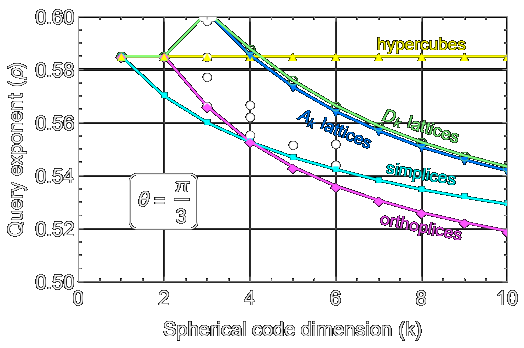
Polytopes, lattices, and spherical codes for the nearest neighbor problem
Thijs LaarhovenICALP 2020 ICALP 2020
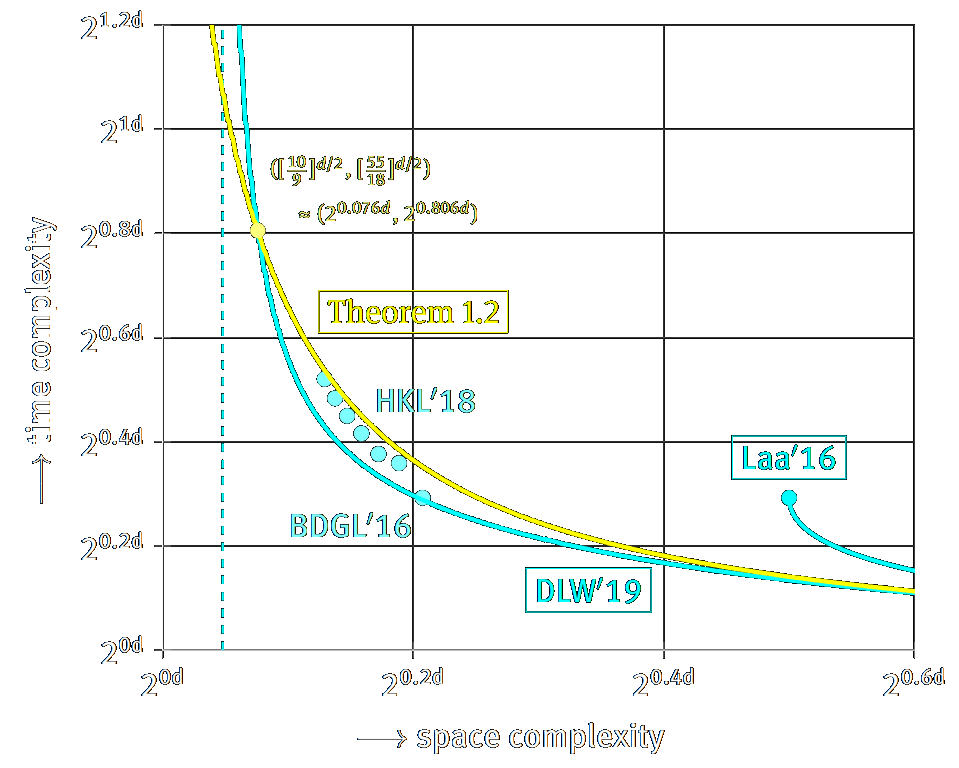
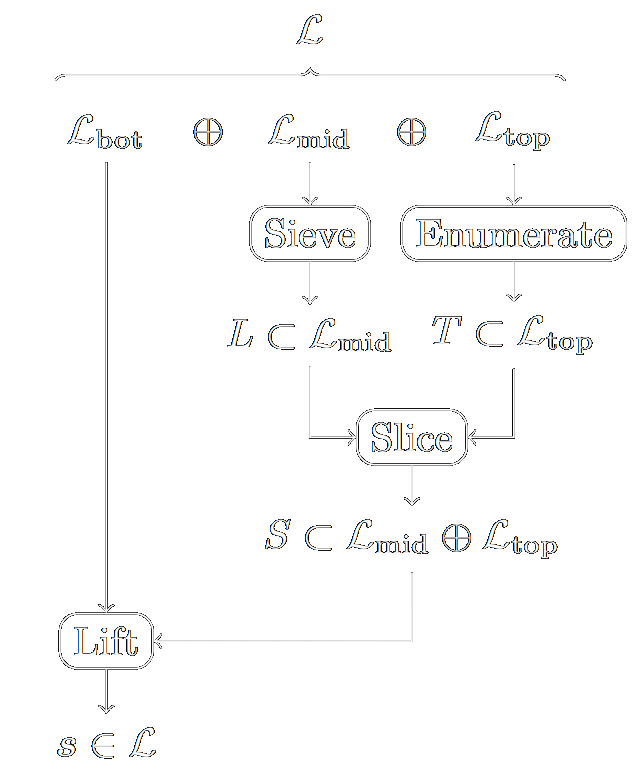
Sieve, enumerate, slice, and lift: Hybrid lattice algorithms for SVP via CVPP
Emmanouil Doulgerakis, Thijs Laarhoven, Benne de WegerAfricaCrypt 2020 AfricaCrypt 2020
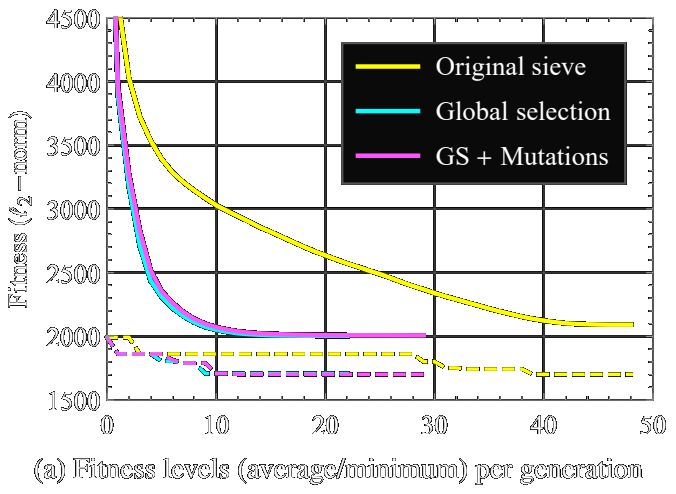
Evolutionary techniques in lattice sieving algorithms
Thijs LaarhovenECTA 2019
Best Paper Award ECTA 2019
Nearest neighbor decoding for Tardos fingerprinting codes
Thijs LaarhovenIH&MMSec 2019 IH&MMSec 2019
Round5: Compact and fast post-quantum public-key encryption
Hayo Baan, Sauvik Bhattacharya, Scott Fluhrer, Óscar García-Morchón, Thijs Laarhoven, Ronald Rietman, Markku-Juhani O. Saarinen, Ludo Tolhuizen, Zhenfei ZhangPQCrypto 2019 PQCrypto 2019
Finding closest lattice vectors using approximate Voronoi cells
Emmanouil Doulgerakis, Thijs Laarhoven, Benne de WegerPQCrypto 2019 PQCrypto 2019
Graph-based time-space trade-offs for approximate near neighbors
Thijs LaarhovenSOCG 2018 SOCG 2018
Progressive lattice sieving
Thijs Laarhoven, Artur MarianoPQCrypto 2018 PQCrypto 2018
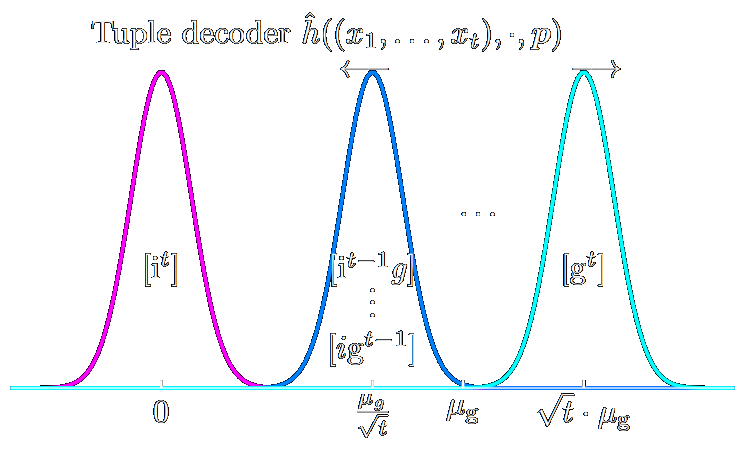
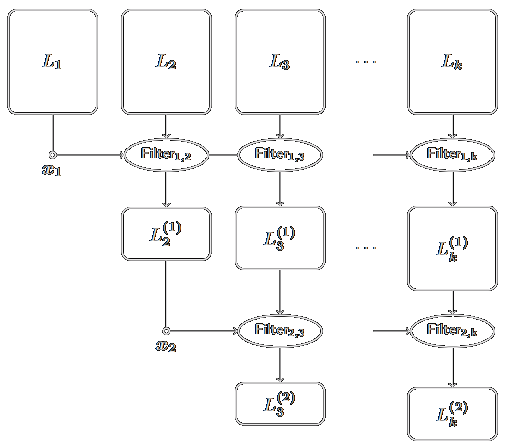
Speed-ups and time-memory trade-offs for tuple lattice sieving
Gottfried Herold, Elena Kirshanova, Thijs LaarhovenPKC 2018 PKC 2018
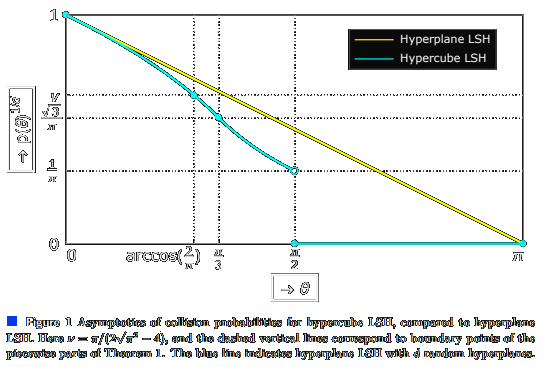
Hypercube LSH for approximate near neighbors
Thijs LaarhovenMFCS 2017 MFCS 2017
A parallel variant of LDSieve for the SVP on lattices
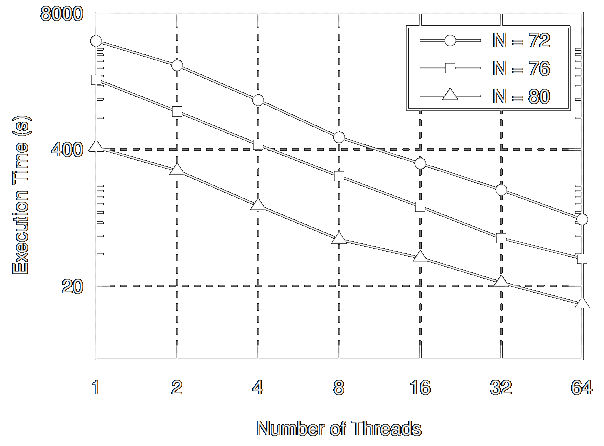
Artur Mariano, Thijs Laarhoven, Christian BischofPDP 2017 PDP 2017
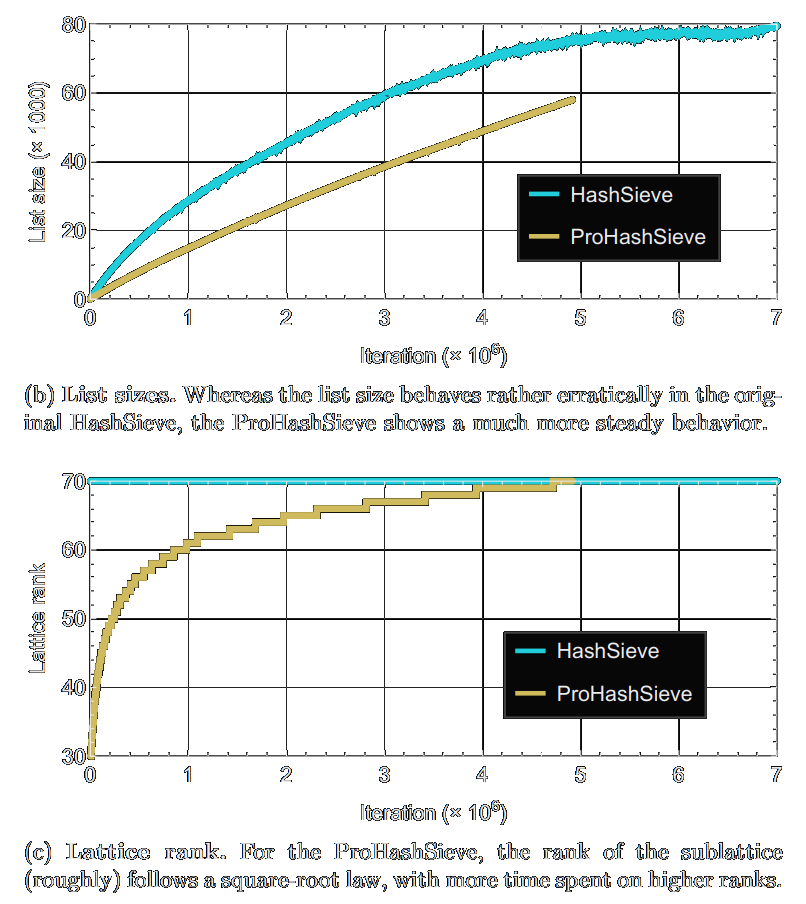
Faster tuple lattice sieving using spherical locality-sensitive filters
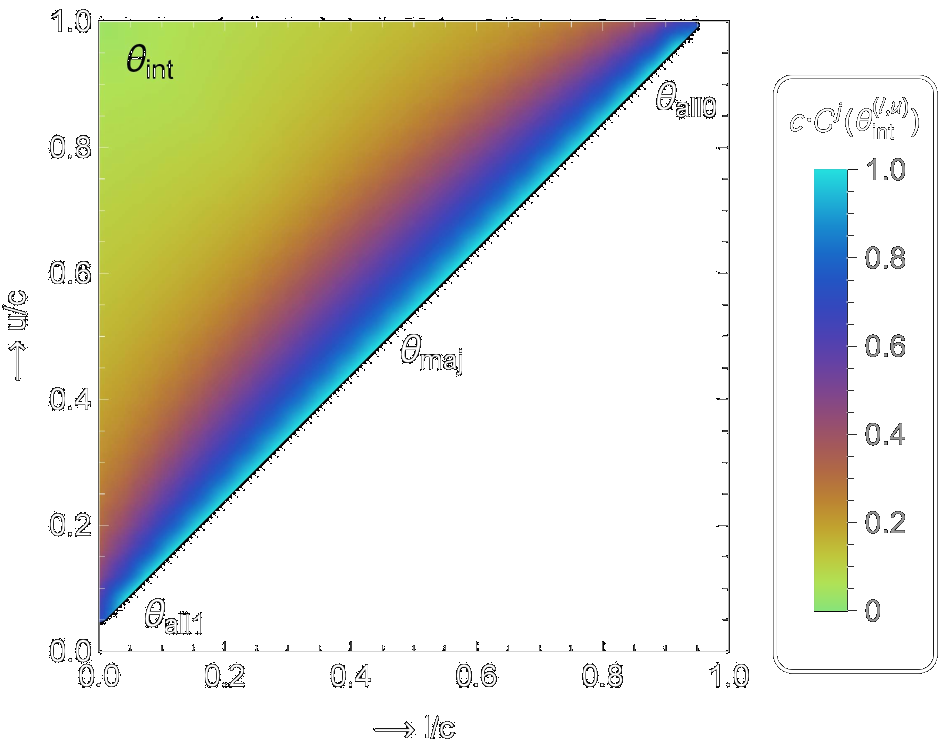
Thijs LaarhovenarXiv:1705.02828 [cs.DS] 2017 arXiv:1705.02828 [cs.DS] 2017
A practical view of the state-of-the-art of lattice-based cryptanalysis
Artur Mariano, Thijs Laarhoven, Fábio Correia, Manuel Rodrigues, Gabriel FalcaoIEEE Access 2017 IEEE Access 2017
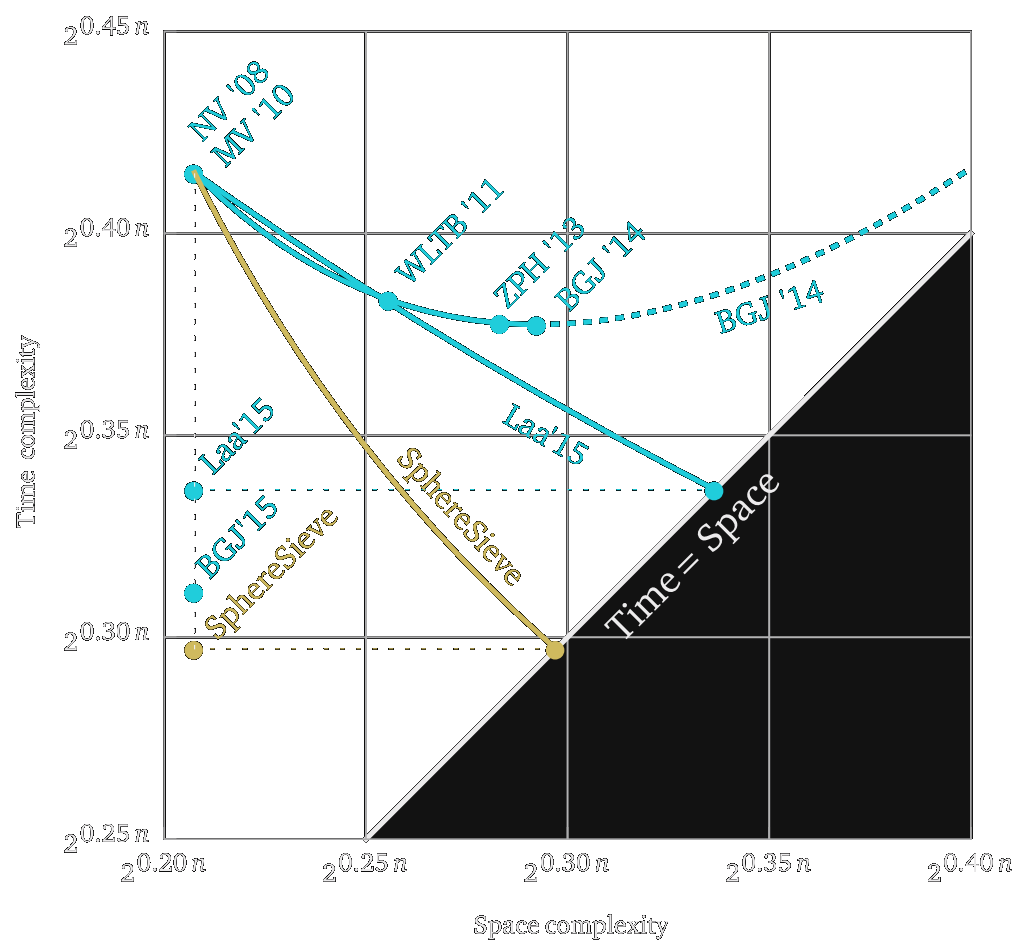
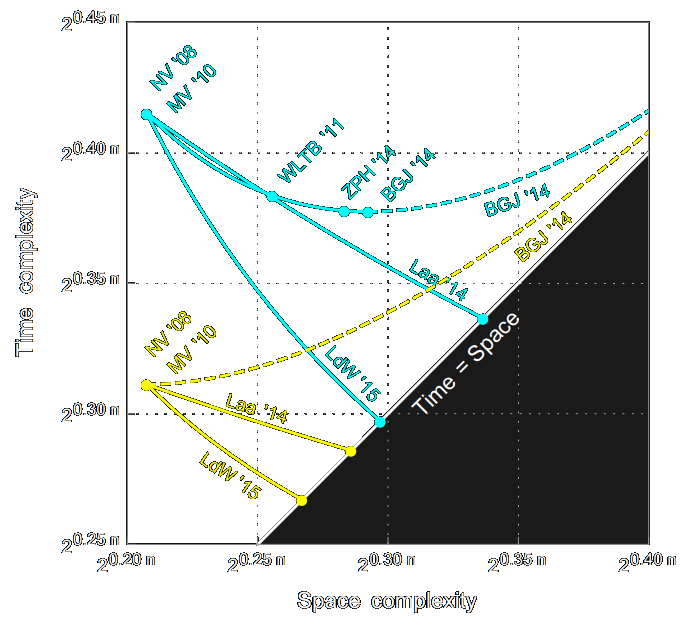
Optimal hashing-based time-space trade-offs for approximate near neighbors
Alexandr Andoni, Thijs Laarhoven, Ilya Razenshteyn, Erik WaingartenSODA 2017
Invited to the ACM Transactions on Algorithms SODA 2017
Sieving for closest lattice vectors (with preprocessing)
Thijs LaarhovenSAC 2016 SAC 2016
Tuple lattice sieving
Shi Bai, Thijs Laarhoven, Damien StehléANTS 2016 ANTS 2016
Lower bounds on time-space trade-offs for approximate near neighbors
Alexandr Andoni, Thijs Laarhoven, Ilya Razenshteyn, Erik WaingartenarXiv:1605.02701 [cs.DS] 2016 arXiv:1605.02701 [cs.DS] 2016
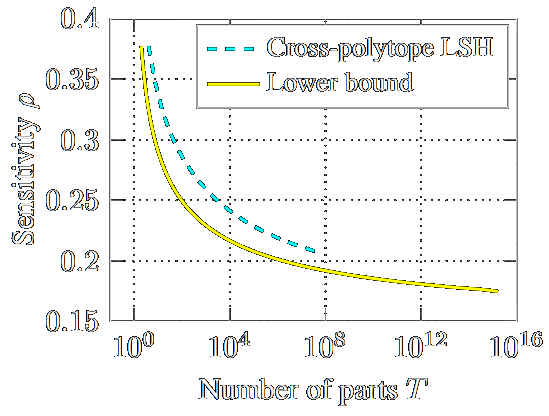
Efficient (ideal) lattice sieving using cross-polytope LSH
Anja Becker, Thijs LaarhovenAfricaCrypt 2016 AfricaCrypt 2016
Search problems in cryptography
Thijs LaarhovenPhD Thesis 2016
Graduated cum laude PhD Thesis 2016
New directions in nearest neighbor searching with applications to lattice sieving
Anja Becker, Léo Ducas, Nicolas Gama, Thijs LaarhovenSODA 2016 SODA 2016
Asymptotics of fingerprinting and group testing: Capacity-achieving log-likelihood decoders
Thijs LaarhovenEURASIP Journal on Information Security 2016 EURASIP Journal on Information Security 2016
Tradeoffs for nearest neighbors on the sphere
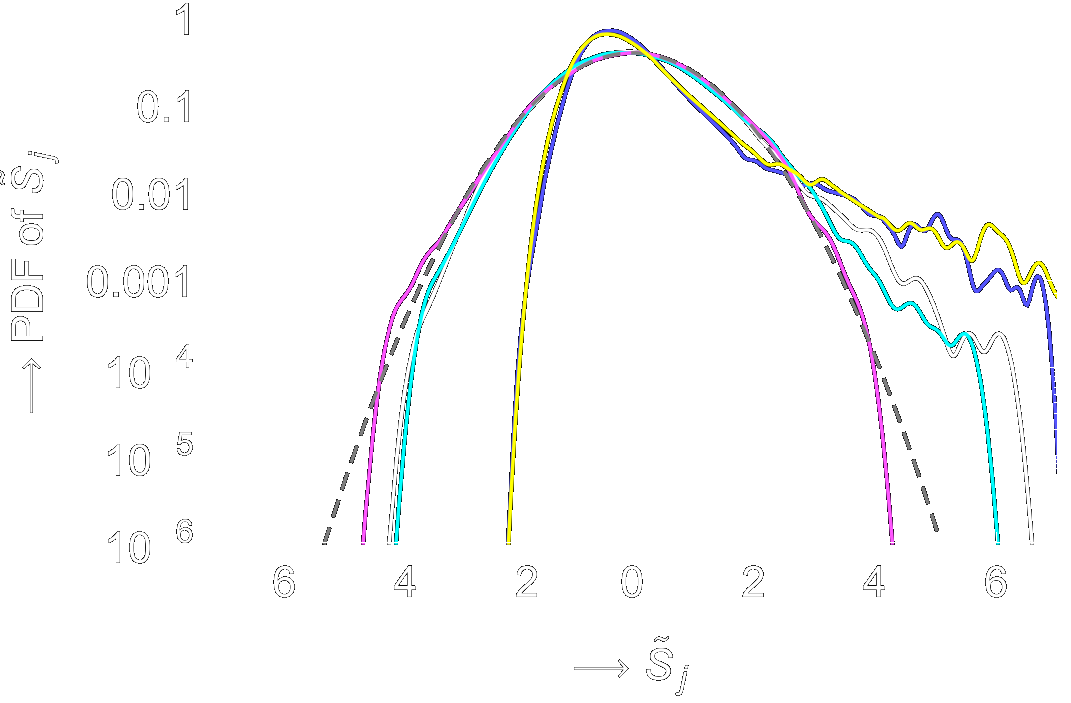
Thijs LaarhovenarXiv:1511.07527 [cs.DS] 2015 arXiv:1511.07527 [cs.DS] 2015
Practical and optimal LSH for angular distance
Alexandr Andoni, Piotr Indyk, Thijs Laarhoven, Ilya Razenshteyn, Ludwig SchmidtNeurIPS 2015 NeurIPS 2015
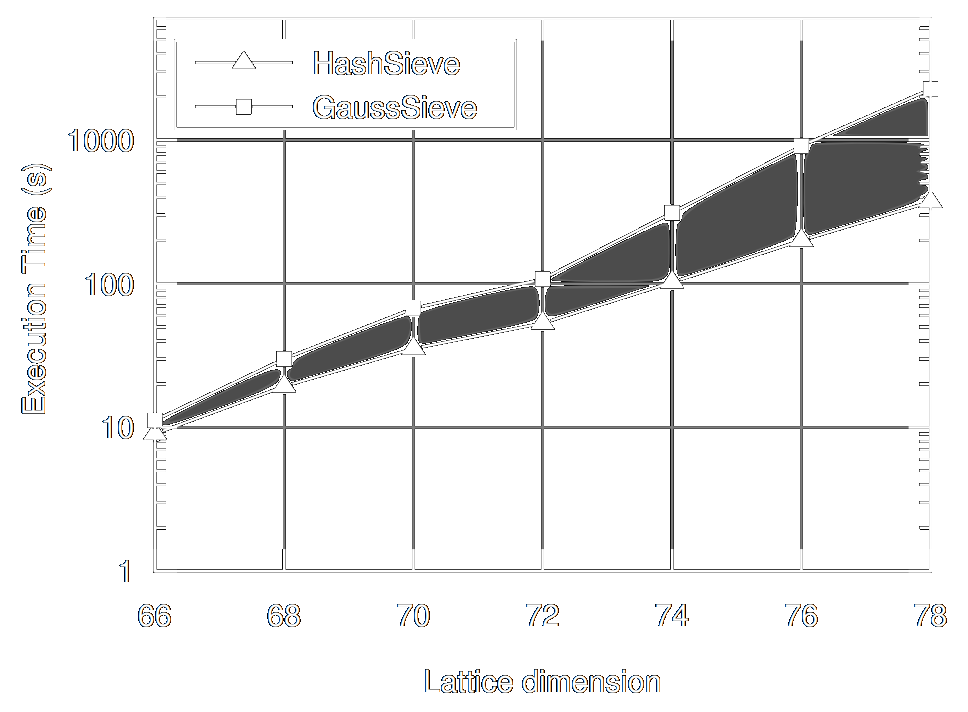
Parallel (probable) lock-free HashSieve: a practical sieving algorithm for the SVP
Artur Mariano, Thijs Laarhoven, Christian BischofICPP 2015 ICPP 2015
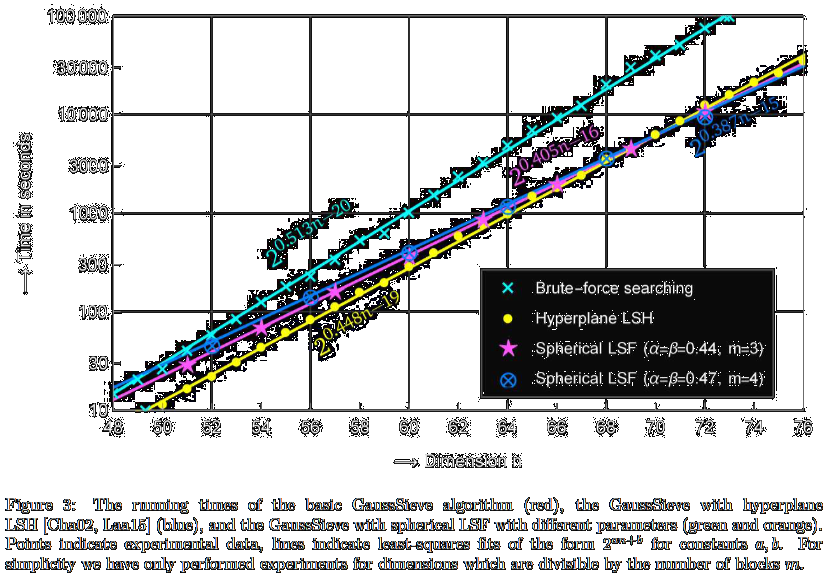
Faster sieving for shortest lattice vectors using spherical locality-sensitive hashing
Thijs Laarhoven, Benne de WegerLatinCrypt 2015 LatinCrypt 2015
Sieving for shortest vectors in lattices using angular locality-sensitive hashing
Thijs LaarhovenCrypto 2015 Crypto 2015
Asymptotics of fingerprinting and group testing: tight bounds from channel capacities
Thijs LaarhovenIEEE Transactions on Information Forensics and Security 2015 IEEE Transactions on Information Forensics and Security 2015
Optimal sequential fingerprinting: Wald vs. Tardos
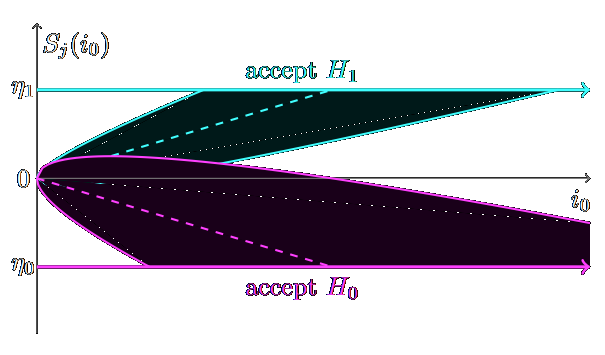
Thijs LaarhovenIH&MMSec 2015
Best Paper Award IH&MMSec 2015
Finding shortest lattice vectors faster using quantum search
Thijs Laarhoven, Michele Mosca, Joop van de PolDesigns, Codes and Cryptography 2015 Designs, Codes and Cryptography 2015
Capacities and capacity-achieving decoders for various fingerprinting games
Thijs LaarhovenIH&MMSec 2014
Best Student Paper Award IH&MMSec 2014
Optimal symmetric Tardos traitor tracing schemes
Thijs Laarhoven, Benne de WegerDesigns, Codes and Cryptography 2014 Designs, Codes and Cryptography 2014
Tuple decoders for traitor tracing schemes
Jan-Jaap Oosterwijk, Jeroen Doumen, Thijs LaarhovenSPIE 2014 SPIE 2014
Dynamic traitor tracing schemes, revisited
Thijs LaarhovenWIFS 2013 WIFS 2013
Efficient probabilistic group testing based on traitor tracing
Thijs LaarhovenAllerton 2013 Allerton 2013
Discrete distributions in the Tardos scheme, revisited
Thijs Laarhoven, Benne de WegerIH&MMSec 2013 IH&MMSec 2013
The Collatz conjecture and De Bruijn graphs
Thijs Laarhoven, Benne de WegerIndagationes Mathematicae 2013 Indagationes Mathematicae 2013
Solving the shortest vector problem in lattices faster using quantum search
Thijs Laarhoven, Michele Mosca, Joop van de PolPQCrypto 2013 PQCrypto 2013
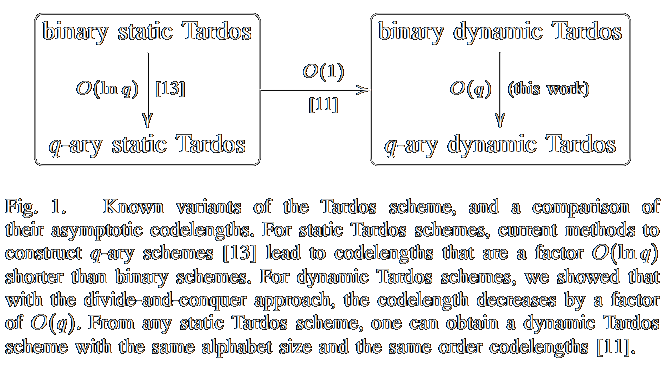
Dynamic Tardos traitor tracing schemes
Thijs Laarhoven, Jeroen Doumen, Peter Roelse, Boris Škorić, Benne de WegerIEEE Transactions on Information Theory 2013 IEEE Transactions on Information Theory 2013
Dynamic traitor tracing for arbitrary alphabets: Divide and conquer
Thijs Laarhoven, Jan-Jaap Oosterwijk, Jeroen DoumenWIFS 2012
Best Paper Award WIFS 2012
Dynamic Tardos traitor tracing schemes
Peter Roelse, Jeroen Doumen, Thijs LaarhovenPatent 2012 Patent 2012
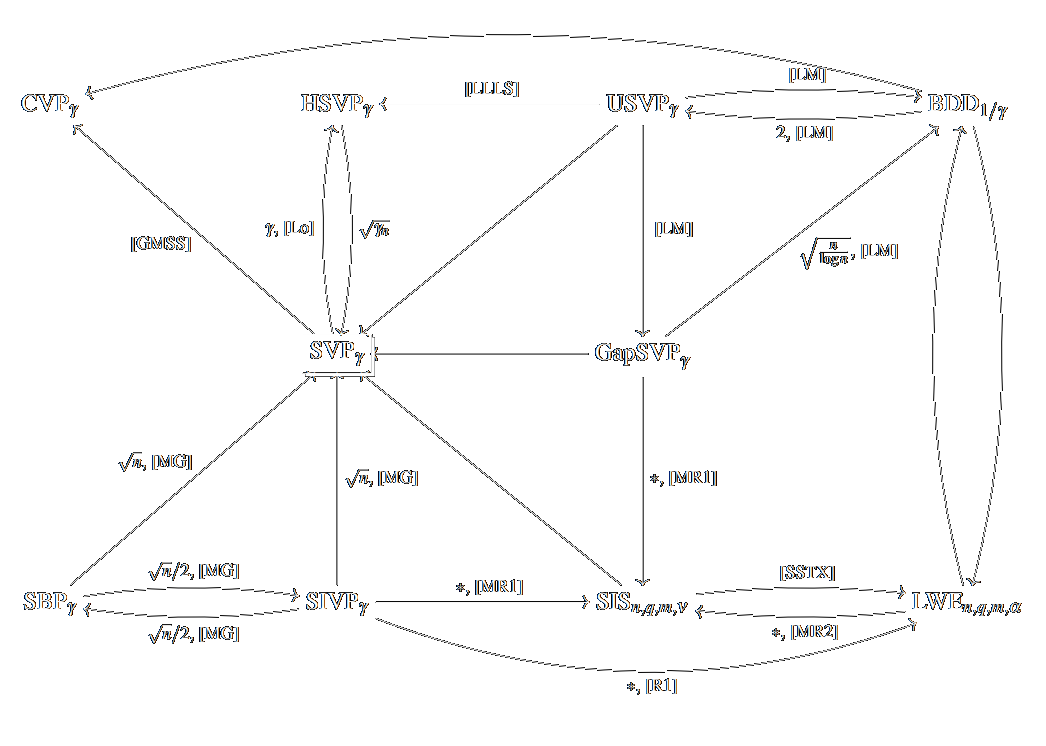
Solving hard lattice problems and the security of lattice-based cryptosystems
Thijs Laarhoven, Joop van de Pol, Benne de WegerCryptology ePrint Archive 2012 Cryptology ePrint Archive 2012
Collusion-resistant traitor tracing schemes
Thijs LaarhovenMaster thesis 2011
Graduated cum laude Master thesis 2011
The 3n+1 conjecture
Thijs LaarhovenBachelor thesis 2009 Bachelor thesis 2009
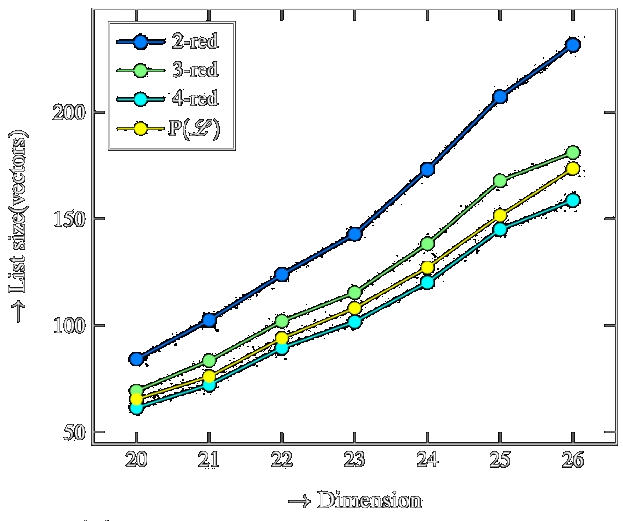
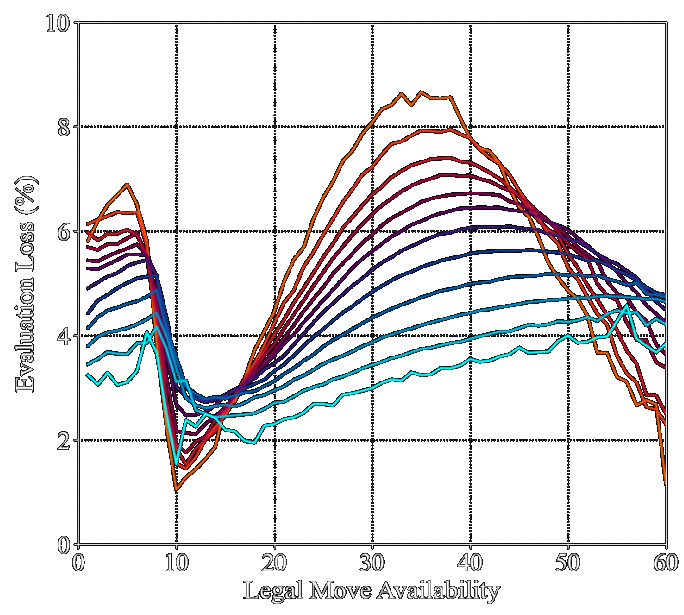
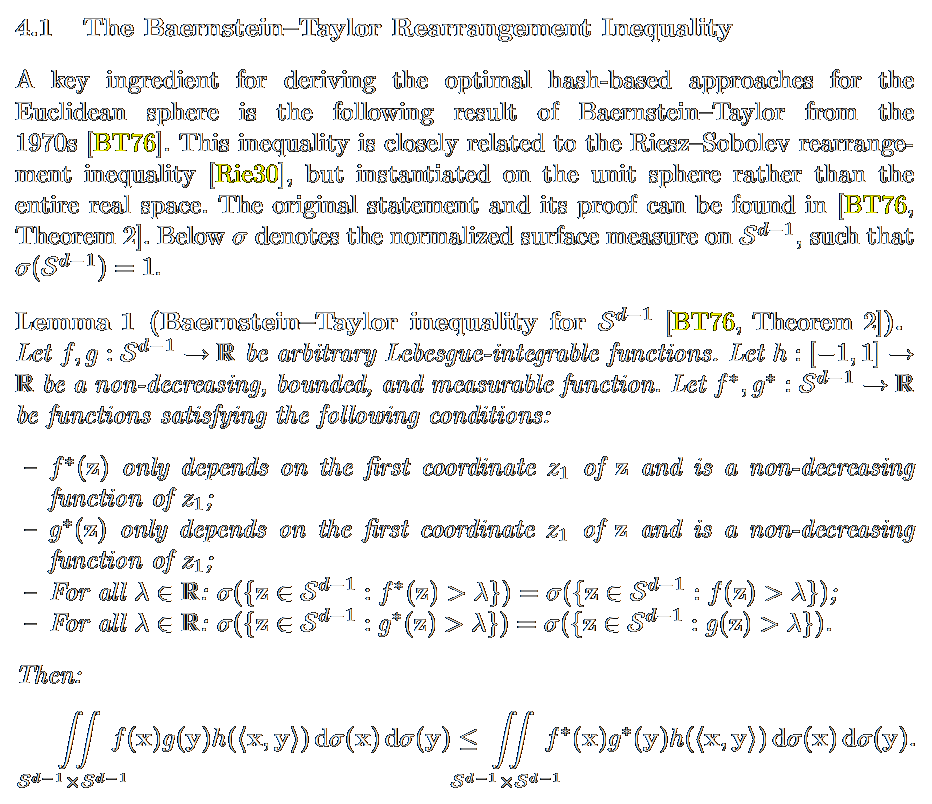
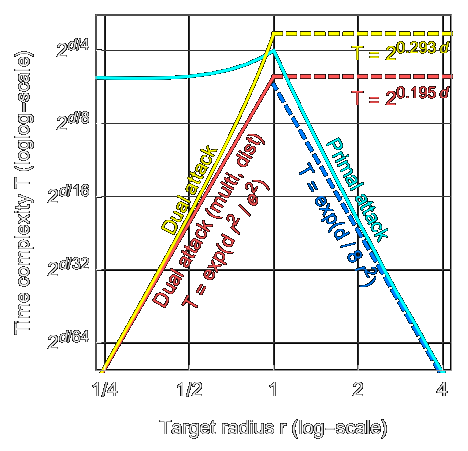
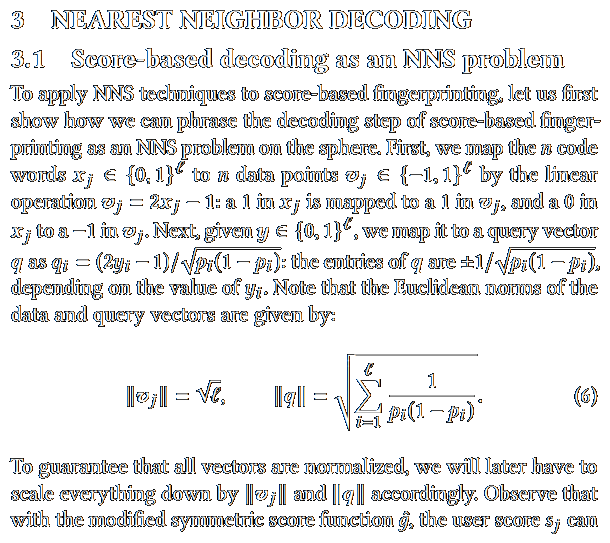
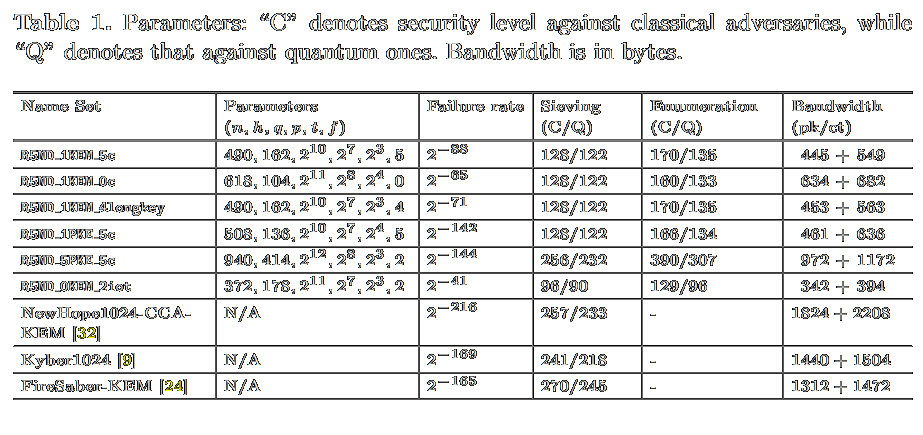
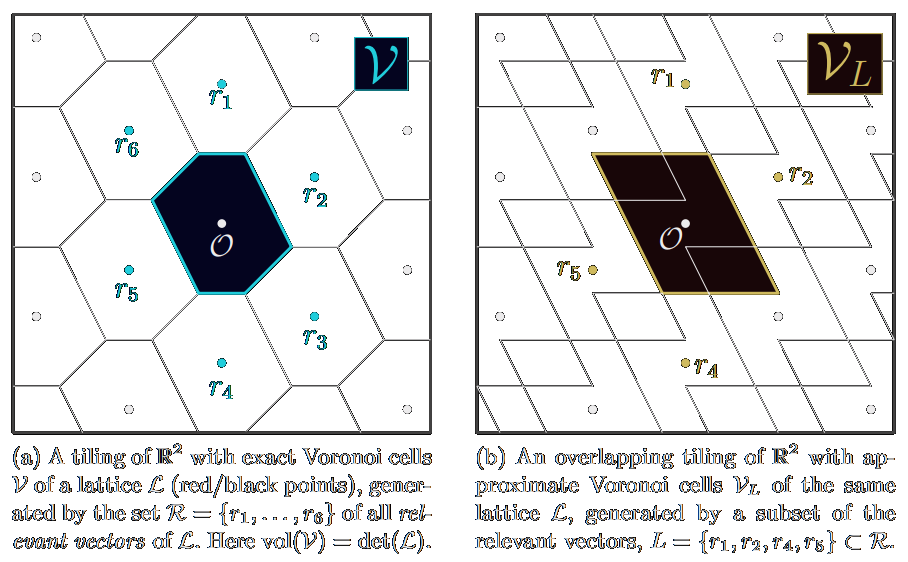
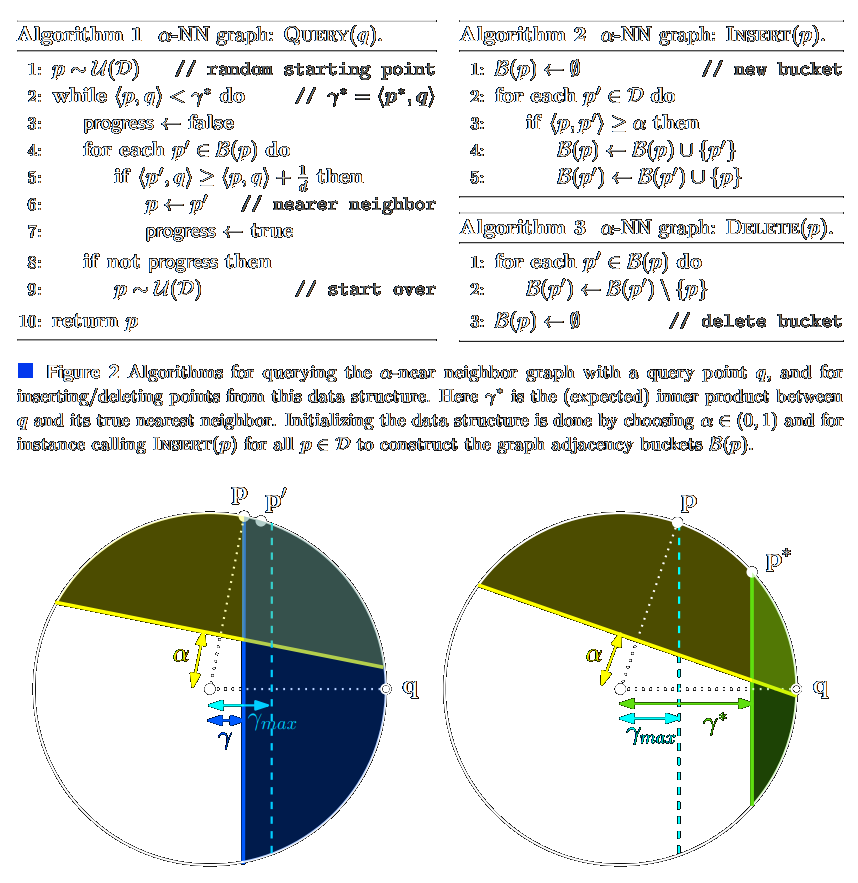
![/ arXiv:1705.02828 [cs.DS] 2017](papers/pnginv/laarhoven17tuple.png)
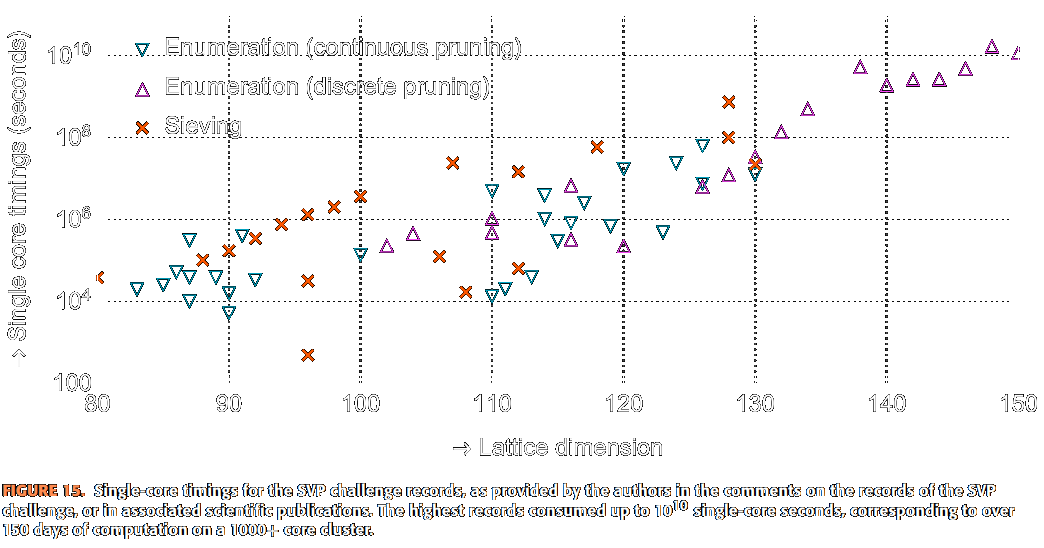
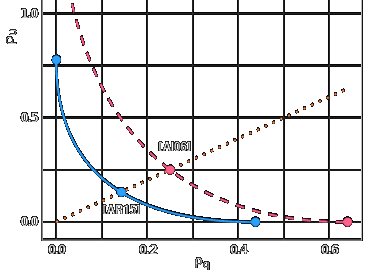
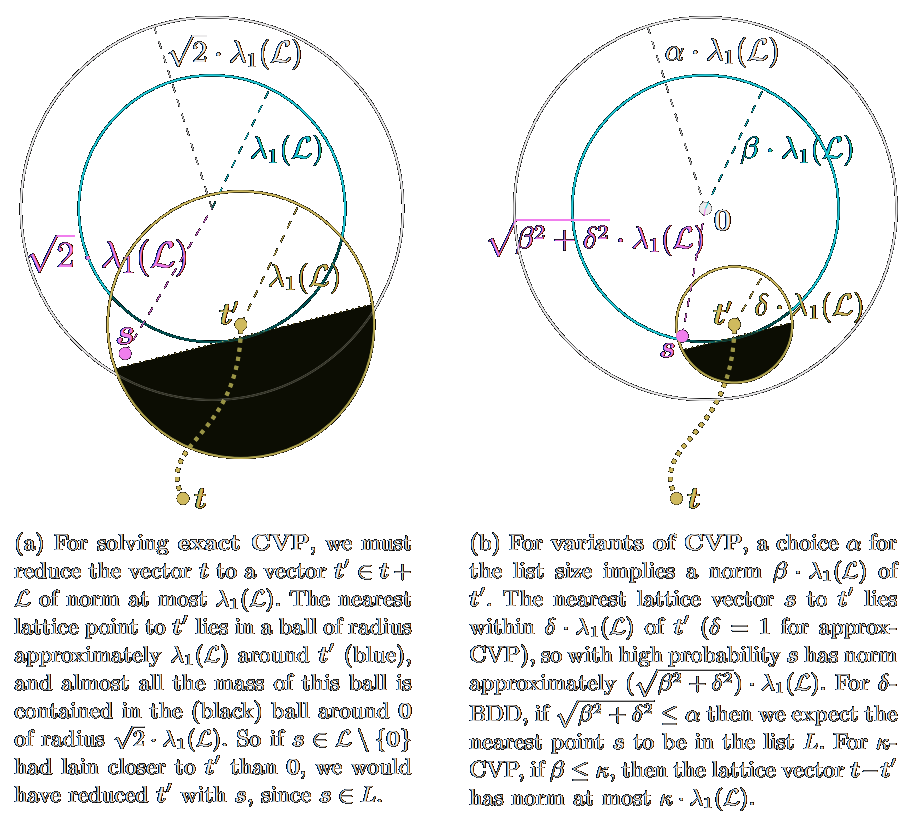
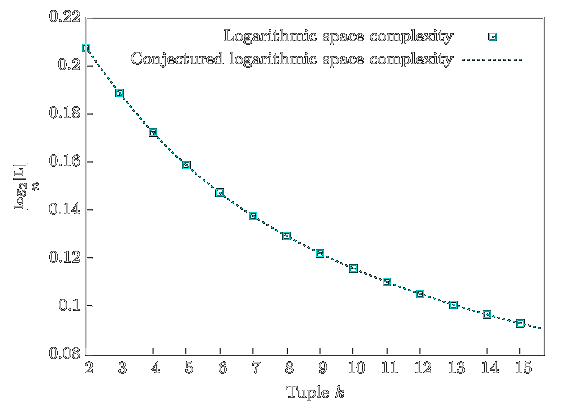
![/ arXiv:1605.02701 [cs.DS] 2016](papers/pnginv/andoni16.png)
![/ arXiv:1511.07527 [cs.DS] 2015](papers/pnginv/laarhoven15nns.png)